In this article
PII: Introduction
PII refers to any information that can be used to identify an individual, either on its own or when combined with other data. This includes obvious elements like full names, social security numbers, and addresses. However, it goes beyond these basic identifiers and extends to more subtle details such as email addresses, phone numbers, and even IP addresses.
In today’s digital age, data privacy has become a crucial concern for individuals and organizations alike. One type of data that holds significant importance is personal identifiable information.
The reason PII is considered sensitive is because it can be exploited by malicious actors for various purposes, including identity theft, fraud, and unauthorized access to personal accounts. Consequently, both individuals and businesses have a responsibility to safeguard PII and ensure its proper handling.
Organizations that collect and store PII are bound by legal obligations to protect this information from unauthorized access or disclosure. They must implement appropriate security measures and adhere to strict data protection regulations.
It’s important to note that PII can take different forms depending on the industry and the context in which it is collected. For example, in the healthcare sector, PII includes medical records, health insurance information, and even biometric data.
Similarly, financial institutions consider account numbers, credit card details, and transaction history as PII. In the online realm, user login credentials like usernames and passwords are also classified as PII.
PII encompasses a wide range of personal information that can be used to uniquely identify individuals. From basic identifiers like names and addresses to more nuanced details such as email addresses and IP addresses, PII requires careful handling and protection.
By understanding what constitutes PII data, individuals and organizations can take the necessary steps to ensure the privacy and security of this sensitive information.
This comprehensive guide will delve into the various aspects of PII data, including its types, the importance of protecting it, the laws and regulations governing it, the risks and threats associated with it, best practices, steps to take in case of a PII data breach, the tools and techniques available for its protection, and how it is used in different industries.
Types of PII data
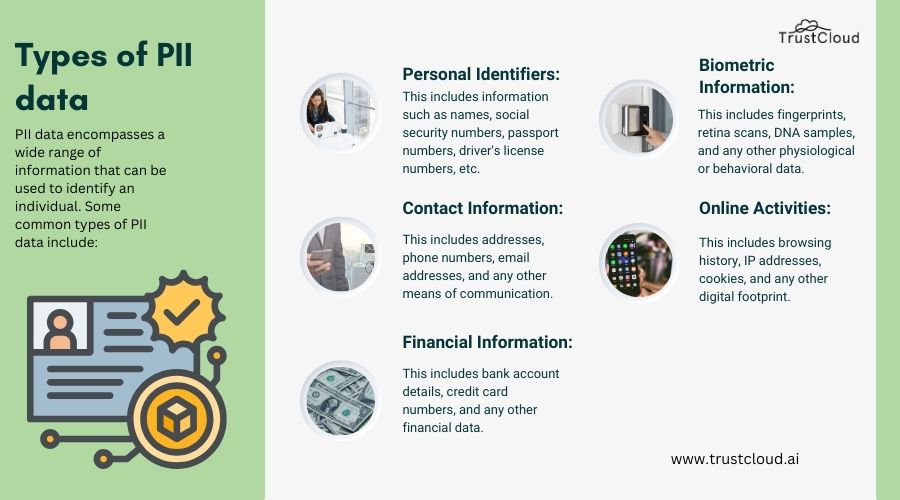
PII data encompasses a wide range of information that can be used to identify an individual.
Some common types of PII data include:
- Personal Identifiers: This includes information such as names, social security numbers, passport numbers, driver’s license numbers, and any other unique identifiers that can be used to distinguish an individual from others.
- Contact Information: This includes addresses, phone numbers, email addresses, and any other means of communication that can be used to reach an individual.
- Financial Information: This includes bank account details, credit card numbers, and any other financial data that can be used to carry out transactions or access funds.
- Biometric Information: This includes fingerprints, retina scans, DNA samples, and any other physiological or behavioral data that can be used to identify an individual.
- Online Activities: This includes browsing history, IP addresses, cookies, and any other digital footprint that can be used to track an individual’s online behavior.
Importance of protecting PII Data
Protecting this data is of utmost importance for both individuals and organizations. Here are some key reasons why safeguarding PII data should be a top priority:
- Identity Theft Prevention: This data is a goldmine for identity thieves. By obtaining someone’s PII data, criminals can impersonate them, commit fraudulent activities, and cause financial and reputational damage.
- Privacy Preservation: This data allows individuals to maintain their privacy and control over their personal information. Protecting it ensures that individuals can trust organizations with their sensitive data without fear of it being misused or mishandled.
- Compliance with Laws and Regulations: Many countries have enacted laws and regulations to protect PII data. Organizations that fail to comply with these laws can face severe legal consequences, including hefty fines and reputational damage.
- Maintaining Customer Trust: Organizations that prioritize the protection of this data build trust with their customers. This trust translates into customer loyalty, positive brand reputation, and a competitive edge in the market.
Laws and regulations
Given the sensitive nature of this data, governments around the world have implemented various laws and regulations to protect its privacy and security. Some notable examples include:
- General Data Protection Regulation (GDPR): The GDPR is a comprehensive data protection law that applies to all European Union (EU) member states. It governs the collection, processing, and storage of PII data and gives individuals greater control over their personal information.
- California Consumer Privacy Act (CCPA): The CCPA is a landmark privacy law in the United States that grants California residents certain rights regarding their PII data. It requires businesses to be transparent about their data practices and provides individuals with the ability to opt-out of data sharing.
- Health Insurance Portability and Accountability Act (HIPAA): HIPAA is a U.S. federal law that protects the privacy and security of individuals’ health information. It sets standards for the handling of PII data by healthcare providers, insurers, and other entities in the healthcare industry.
- Personal Data Protection Act (PDPA): The PDPA is a data protection law in Singapore that governs the collection, use, and disclosure of personal data. It establishes rules for organizations on obtaining consent, ensuring accuracy, and protecting PII data.
Associated risks and threats
PII data faces numerous risks and threats that can compromise its privacy and security. Here are some common risks and threats associated with PII data:
- Data Breaches: One of the most significant risks to PII data is a data breach. Hackers and cybercriminals target organizations to gain unauthorized access to PII data, which can then be sold on the dark web or used for malicious purposes.
- Phishing Attacks: Phishing attacks involve tricking individuals into revealing their PII data through fraudulent emails or websites. These attacks are often sophisticated and can result in significant data loss and financial harm.
- Insider Threats: Employees or insiders with access to PII data can intentionally or unintentionally misuse or mishandle it. This can lead to data breaches, identity theft, or other forms of data misuse.
- Third-Party Risks: Organizations often share PII data with third-party vendors or service providers. If these third parties have weak security measures in place, they can become a potential entry point for attackers to gain access to PII data.
Best Practices for Handling and Securing
To ensure the privacy and security of PII data, organizations should adopt best practices for its handling and safeguarding. Here are some essential practices to consider:
- Data Minimization: Only collect and retain the data that is necessary for business purposes. Avoid storing excessive amounts of data that could be a target for attackers.
- Encryption: Encrypt data at rest and in transit to protect it from unauthorized access. Implement strong encryption algorithms and ensure that encryption keys are securely managed.
- Access Control: Implement strict access controls to limit who can access data. Use strong authentication mechanisms, such as multi-factor authentication, and regularly review and revoke unnecessary access privileges.
- Data Breach Response Plan: Develop a comprehensive data breach response plan that outlines the steps to be taken in the event of a data breach. This includes notifying affected individuals, cooperating with law enforcement, and conducting a thorough investigation.
Steps to take in the event of a data breach
Despite the best preventive measures, PII data breaches can still occur. In the event of a breach, it is crucial to take immediate action to mitigate the damage. Here are the steps to follow:
- Containment: Immediately isolate and secure the affected systems to prevent further unauthorized access to PII data. This may involve disconnecting affected servers or taking them offline temporarily.
- Notification: Notify affected individuals as soon as possible, providing them with clear and concise information about the breach and the steps they should take to protect themselves. This may include changing passwords, monitoring financial accounts, or freezing credit.
- Investigation: Conduct a thorough investigation to determine the cause and extent of the breach. This may involve working with cybersecurity experts and law enforcement agencies to identify the attackers and prevent future breaches.
- Remediation: Take appropriate measures to remediate the breach, such as patching vulnerabilities, enhancing security controls, and implementing stronger safeguards to prevent similar incidents in the future.
PII Data protection tools and techniques
To effectively protect data, organizations can leverage a range of tools and techniques. Here are some commonly used ones:
- Data Loss Prevention (DLP) Solutions: DLP solutions help organizations identify, monitor, and protect sensitive data, including PII data. They can detect and prevent unauthorized data transfers, encrypt data, and enforce data handling policies.
- Encryption Technologies: Encryption technologies ensure that data remains secure even if it falls into the wrong hands. By encrypting data both at rest and in transit, organizations can mitigate the risk of unauthorized access.
- Identity and Access Management (IAM) Systems: IAM systems enable organizations to manage user identities and control access to data. They help ensure that only authorized individuals can access sensitive information.
- Security Awareness Training: Educating employees about the importance of PII data protection and providing them with training on how to identify and respond to potential threats can significantly enhance an organization’s security posture.
PII Data in Different Industries
This data is not confined to a particular industry; it is prevalent in various sectors. Here are some examples of how PII data is used in different industries:
- Healthcare: In the healthcare industry, this data is essential for providing quality care and ensuring patient privacy. It includes medical records, health insurance information, and other sensitive data necessary for diagnosis and treatment.
- Financial Services: Banks, credit card companies, and other financial institutions collect and process vast amounts of this data. This includes customer account information, transaction history, and credit scores.
- E-commerce: Online retailers collect data to facilitate transactions, deliver products, and provide personalized shopping experiences. This includes customer names, shipping addresses, and payment details.
- Social Media: Social media platforms gather extensive data from their users, including personal profiles, photos, and preferences. This data is used for targeted advertising and content personalization.
Conclusion: Safeguarding PII data for a secure digital future
As technology continues to advance, the protection of PII data becomes increasingly critical. Organizations and individuals must take proactive measures to safeguard this sensitive information from unauthorized access and misuse.
With the best practices for handling and securing it and the tools and techniques available for its protection, we can create a secure digital future where privacy and security are prioritized. Let us all work together to protect our data and ensure a safe and trusted digital environment.
Sign up with TrustCloud to learn more about how you can upgrade GRC into a profit center by automating your organization’s governance, risk management, and compliance processes.
Explore our GRC launchpad to gain expertise on numerous GRC topics and compliance standards.