Why every organization needs an Acceptable Use Policy (AUP): Exploring legal and security implications
An AUP that is Acceptable Use Policy is a vital tool that every organization should adopt. In today’s digital landscape, organizations face numerous legal and security challenges. To mitigate these risks, an Acceptable Use Policy (AUP) is developed. This policy serves as a set of guidelines that dictate how employees and users can utilize company resources, such as computers, networks, and internet access.
Legal Implications of Not Having an Acceptable Use Policy
Without an Acceptable Use Policy in place, organizations expose themselves to significant legal risks. Firstly, the absence of an AUP can make it difficult to hold employees accountable for their actions when using company resources. This lack of clarity can lead to misuse and even illegal activities, such as copyright infringement, harassment, or dissemination of confidential information.
In addition, without a clear AUP, employees may inadvertently engage in activities that violate laws or regulations. For instance, downloading copyrighted material without permission can result in legal consequences for both the individual and the organization. Without an AUP to outline these boundaries, employees may unknowingly engage in activities that expose the organization to potential lawsuits.
Furthermore, in the absence of an AUP, organizations may struggle to defend themselves against claims of negligence. If an employee’s misuse of company resources leads to harm or loss for another party, the organization can be held liable for failing to establish guidelines and enforce compliance.
To avoid these legal pitfalls, having a well-crafted AUP is essential. By clearly outlining acceptable behavior and the legal consequences of non-compliance, organizations can protect themselves from legal liabilities and ensure employees understand their responsibilities.
Security Implications of Not Having an Acceptable Use Policy
In today’s interconnected world, organizations face an ever-increasing number of security threats. Without an Acceptable Use Policy, organizations leave their networks, systems, and sensitive data vulnerable to unauthorized access, data breaches, and other cyber-attacks.
An AUP plays a crucial role in safeguarding an organization’s digital assets. By clearly defining acceptable and prohibited activities, an AUP helps establish a security-conscious culture within the organization. It educates employees about the potential risks involved in their digital interactions and provides guidelines for protecting sensitive information.
Without a comprehensive AUP, employees may unknowingly engage in actions that compromise the organization’s security. This can include clicking on suspicious links, downloading malicious files, or sharing sensitive information with unauthorized individuals. These actions can lead to malware infections, data breaches, or even the compromise of the entire network.
Furthermore, the absence of an AUP can hinder an organization’s ability to respond effectively to security incidents. Without clear guidelines in place, employees may not know how to report suspicious activities or handle security breaches. This lack of awareness and preparedness can delay incident response and exacerbate the impact of a security incident.
By implementing and enforcing an AUP, organizations can significantly reduce the risk of security incidents. It helps employees understand their responsibilities in maintaining a secure digital environment and provides guidelines for preventing and reporting security breaches.
Benefits of Having an Acceptable Use Policy
Having a well-crafted Acceptable Use Policy offers numerous benefits for organizations. Firstly, it establishes clear boundaries for acceptable behavior, promoting a productive and respectful work environment. By defining what constitutes acceptable use of company resources, an AUP helps prevent misuse or abuse, such as excessive personal use of the internet or social media during work hours.
Secondly, an AUP helps protect an organization’s reputation by preventing employees from engaging in activities that could damage the company’s image. By outlining guidelines for appropriate online behavior, organizations can ensure that employees are representing the company in a professional manner, both internally and externally.
Furthermore, an AUP plays a crucial role in protecting the organization’s sensitive data and intellectual property. By clearly stating the importance of data security and outlining procedures for handling confidential information, an AUP reduces the risk of data breaches and unauthorized access.
Additionally, an AUP helps educate employees about the potential risks associated with using company resources and the internet. By raising awareness of cybersecurity threats, employees become more vigilant and are less likely to fall victim to phishing attempts, malware, or other cyber-attacks.
Overall, implementing an AUP demonstrates an organization’s commitment to maintaining a safe and secure digital environment, ultimately fostering trust among employees, clients, and stakeholders.
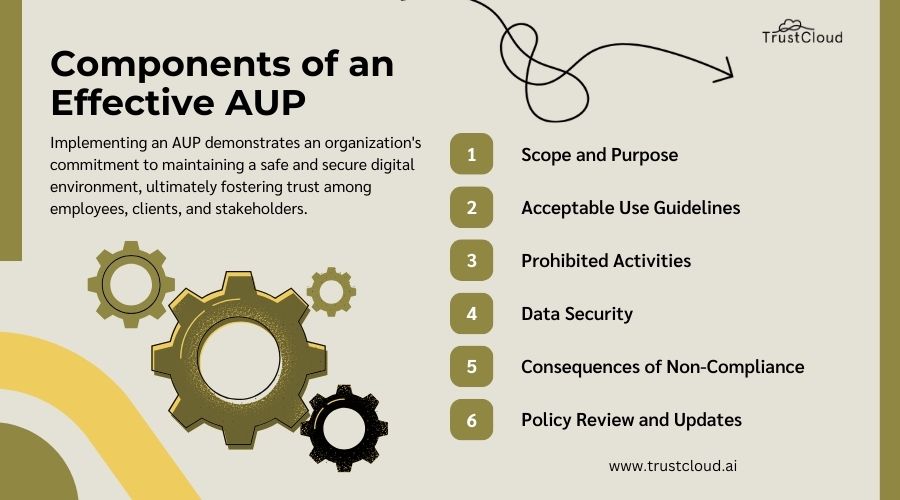
Components of an Effective Acceptable Use Policy
To ensure the effectiveness of an Acceptable Use Policy, several key components should be included.
These components are:
- Scope and Purpose: Clearly define the purpose of the AUP and specify the resources and activities it covers. This section should also outline who the policy applies to, such as employees, contractors, and visitors.
- Acceptable Use Guidelines: Provide detailed guidelines on what constitutes acceptable use of company resources, including computers, networks, internet access, and email. This section should cover topics such as appropriate online behavior, personal use of company resources, and the use of social media.
- Prohibited Activities: Clearly state activities that are strictly prohibited, such as accessing or distributing illegal content, engaging in cyberbullying or harassment, or attempting unauthorized access to systems or data.
- Data Security: Outline the importance of data security and specify procedures for handling sensitive information. This should include guidelines for password management, data backup practices, and reporting security incidents.
- Consequences of Non-Compliance: Clearly communicate the consequences of violating the AUP, including disciplinary actions that may be taken. This section should also detail the process for reporting violations and the steps involved in investigating and resolving incidents.
- Policy Review and Updates: Specify how often the AUP will be reviewed and updated, ensuring that it remains relevant and effective in addressing emerging security threats and legal requirements.
By including these components in an AUP, organizations can create a comprehensive policy that addresses both legal and security considerations.
Tips for Creating an Acceptable Use Policy
When creating an Acceptable Use Policy, organizations should keep the following tips in mind:
- Involve Relevant Stakeholders: Consult with legal, HR, IT, and other departments to ensure that the AUP addresses all necessary legal and security requirements.
- Use Clear and Concise Language: Make sure the AUP is written in plain language that is easily understandable by all employees. Avoid technical jargon or complex legal terms.
- Educate Employees: Provide training and awareness programs to ensure that all employees understand the AUP and their responsibilities. Regularly communicate updates and reminders to reinforce compliance.
- Tailor the AUP to the Organization: Customize the AUP to reflect the unique needs and culture of the organization. Consider industry-specific regulations, the organization’s risk appetite, and the specific digital resources being used.
- Seek Legal Review: Have the AUP reviewed by legal counsel to ensure it complies with relevant laws and regulations. This step is particularly important when dealing with international or industry-specific compliance requirements.
By following these tips, organizations can create an AUP that is tailored to their specific needs and effectively addresses legal and security considerations.
How to Enforce an Acceptable Use Policy
Enforcing an Acceptable Use Policy requires a proactive and consistent approach. Here are some steps organizations can take to ensure compliance:
- Communicate the AUP: Clearly communicate the AUP to all employees and require them to acknowledge their understanding and agreement. This can be done through training sessions, email notifications, or electronic signatures.
- Monitor and Audit: Regularly monitor and audit network traffic, system logs, and user activities to identify any potential violations. This can be done using security tools, employee monitoring software, or manual checks.
- Report and Investigate: Establish a process for employees to report suspected violations and ensure that all reports are promptly investigated. This encourages a culture of accountability and helps identify potential security incidents early.
- Enforce Consequences: Consistently apply the consequences outlined in the AUP for violations. This may include verbal warnings, written reprimands, suspension, or termination, depending on the severity of the offense.
- Update and Educate: Continuously update the AUP to address emerging security threats and legal requirements. Regularly educate employees on the importance of compliance and provide training on new policies or updates.
By enforcing the AUP in a fair and consistent manner, organizations can demonstrate their commitment to maintaining a secure digital environment and encourage employees to adhere to the policy.
Case Studies: Organizations That Suffered Due to Lack of an AUP
Several high-profile cases demonstrate the consequences of not having an Acceptable Use Policy in place. One such example is a multinational company that faced a significant data breach due to an employee unknowingly clicking on a malicious link. The absence of an AUP meant that the employee was not adequately trained to recognize phishing attempts, leading to the compromise of sensitive customer data.
In another case, a small business faced legal consequences when an employee engaged in cyberbullying through company email accounts. The lack of an AUP made it difficult for the organization to hold the employee accountable or defend against claims of negligence, resulting in reputational damage and legal expenses.
These case studies highlight the potential risks and negative consequences organizations face when they neglect to implement an AUP. The impact can range from financial losses and legal liabilities to reputational damage and loss of customer trust.
Resources for Creating an Acceptable Use Policy
Creating an effective Acceptable Use Policy may seem daunting, but there are resources available to help organizations develop a comprehensive and tailored AUP. Here are some recommended resources:
- Industry Associations: Many industry associations provide guidelines and templates for creating AUPs specific to their sector. These resources often incorporate industry-specific compliance requirements and best practices.
- Legal Counsel: Engage legal counsel with expertise in technology and employment law to ensure the AUP complies with relevant regulations and addresses legal considerations.
- Cybersecurity Organizations: Organizations specializing in cybersecurity often provide resources and best practices for creating AUPs that address the latest security threats and vulnerabilities.
- Government Agencies: Government agencies, such as the Federal Trade Commission (FTC) or the National Institute of Standards and Technology (NIST), offer guidelines and resources for creating AUPs that comply with legal and security standards.
Utilizing these resources can help organizations develop an AUP that is robust, effective, and aligned with industry best practices.
Conclusion
In today’s digital landscape, an Acceptable Use Policy is a crucial tool for organizations to mitigate legal and security risks. By establishing boundaries for acceptable behavior and clearly defining the consequences of non-compliance, an AUP protects organizations from legal liabilities and helps safeguard sensitive data. Additionally, an AUP promotes a security-conscious culture, reducing the risk of security incidents and ensuring employees are aware of their responsibilities. By following best practices, involving relevant stakeholders, and consistently enforcing the AUP, organizations can create a safe and secure digital environment that fosters productivity and trust assurance. Implementing an AUP should be a priority for every organization, regardless of size or industry, to navigate the complex digital landscape and protect their interests.
Sign up with TrustCloud to learn more about how you can upgrade GRC into a profit center by automating your organization’s governance, risk management, and compliance processes.
Explore our GRC launchpad to gain expertise on numerous GRC topics and compliance standards.